USAY Data Security Series
Operation and Maintenance Real-Time Desensitization Platform
Introduction
With the development of the Internet and data industry, more and more analysis and data mining rely on the real production data based on the use of data, data is facing the problem of data security. In order to ensure the use of data by data analysts and reduce the risk of data leakage, USAY has introduced the USAY Operation Platform after longterm research and design.
Product Overview
USAY Operation Platform is a set of private data discovery, data extraction, data bleaching, test data management, data loading and other functions in one platform, combined with access control, performance monitoring and other means to filter user data, and according to user-defined de-sensitization rules to replace the privacy data, to avoid the risk of sensitive data leakage, to ensure the business integrity and effectiveness of test data.
USAY Advantage
Focus on R&D, sales and service of database systems and data related software.
Operation and Maintenance Desensitization Platform Physical Deployment
The operation personnel send the operation and maintenance instructions to USAY desensitization platform. According to the operation instructions, the USAY desensitization platform finds the corresponding and maintenance SQL query statement. The platform sends the SQL query statement to the production statement. The production database sends the result data set of SQL detection to the desensitization platform. With the desensitization rules as constraints, the returned data set is desensitized.
Operation SQL: management, configuration and use
- You can freely classify the operation SQL’s input parameters, and can bulk import and export SQL.
- Quickly select from the operational SQL list.
Operation, maintenance division, and authority
The administrator adds operations; SQL to personalize the classification of all operations. SQL administrators can desensitize the collection of the query results.
USAY Data Desensitization Platform
Introduction
With the development of enterprise business, the business production system has accumulated a large amount of sensitive information including customers, accounts, policies and other sensitive information. This data, for example, is used in many work scenarios, such as business analysis, development testing, audit supervision, and even outsourcing, using real business data and information. If these data are leaked and damaged, it will not only bring economic losses to the enterprise, but also greatly affect the trust of users in the enterprise. How to ensure the safety of production data has become an important problem that enterprises must face.
The Goal of Data Desensitization System Construction
Construction of a data desensitization system is undertaken in order to achieve safe and controllable use of data. The objectives include safe production – which helps customers to build a secure data desensitization environment that prevents the leakage of sensitive data without compromising efficiency. Permission control – access control and desensitization of sensitive data as needed. Business relevance – to maximize the nature and relevance of the business during the desensitization of data. Rapid implementation – implement desensitization system in a short period of time to improve the efficiency of business test data acquisition.
Products and Tools
1. Data Desensitization Process
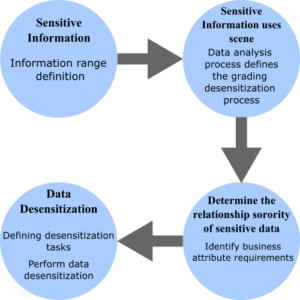
2. Product Characteristics
– Supports library-to-library, library-to-file, file-to-file, file-to-library conversion and publishing methods.
– Supports 1 to 1, 1 to many, many to many, many to 1 of a variety of test data release configuration.
– Supports flexible configuration methods, including field information matching, data information matching, to automatically detect database sensitive information fields.
3. The Core Function of the Product
– Maximum business relevance in the process of desensitization: It looks like real data.
– The data’s primary and foreign key relationships are consistent.
– Retain data distribution characteristics
4. Product Advantages
– Mature and perfect function, high degree of integration, automatic processing of a variety of data, data correlation and other issues.
– Friendly user interface that greatly reduces the user’s skill requirements.
– Intelligent privacy.
– Data discovery technology privacy.
– Data algorithms.
– Deep compression technology.
– Heterogeneous data platform.
– Support distributed scaling.
